Invite a friend (or colleague) and collaborate
You can use subshare in a team or with friends/family to share your data.
In order to demonstrate this, the following example shows how Adam sets up a repository and invites his girl-friend Amélie.
Adam (the repository’s owner) gets started
Adam installs subshare and creates a repository, following the Getting started guide.
Amélie (the invited friend) needs an OpenPGP key, too
The easiest way for Amélie to create an OpenPGP key is to start subshare and follow the setup wizard (see: Getting started). She also should enter the subshare server’s URL, because Adam can then download her key easily within subshare.
If Amélie already possesses an OpenPGP key and Adam already has it in his key-ring, this is not necessary.
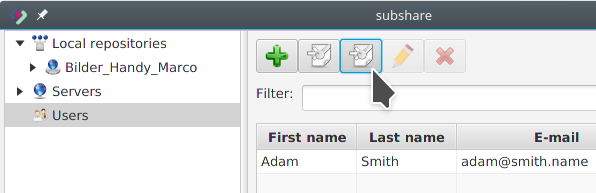
Adam imports Amélie’s OpenPGP key (step 1)
Before Adam can invite Amélie, he needs to retrieve her OpenPGP key. Therefore, he selects Users and clicks the Import key from server button:
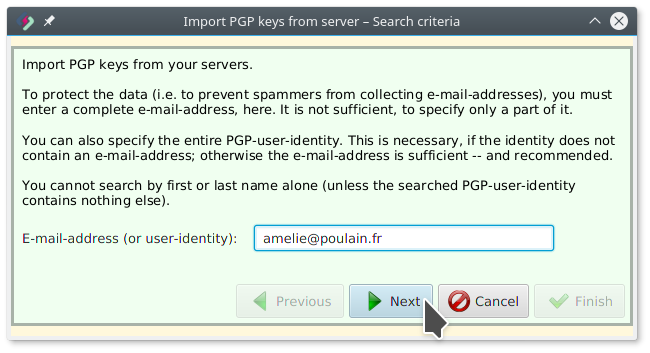
Adam imports Amélie’s OpenPGP key (step 2)
Adam enters Amélie’s e-mail-address and clicks Next:
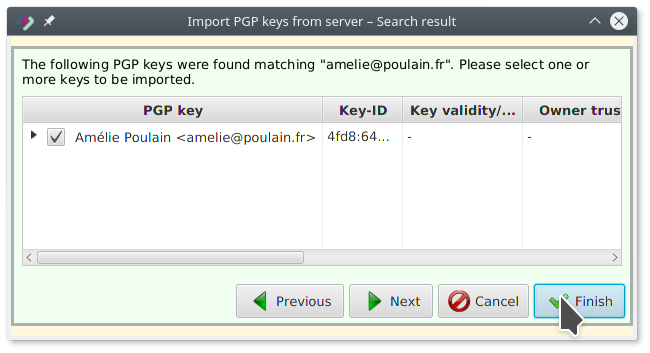
Adam imports Amélie’s OpenPGP key (step 3)
Amélie’s key was found. Finish imports it into Adam’s key-ring:
Adam certifies Amélie’s key (step 1)
It is not required but strongly recommended to verify and sign the downloaded key. Otherwise it’s possible for an attacker to trick Adam into using a fake key and thus allow the attacker to read/write data.
To verify and sign the key, Adam selects Amélie’s key and klicks the Certify button:
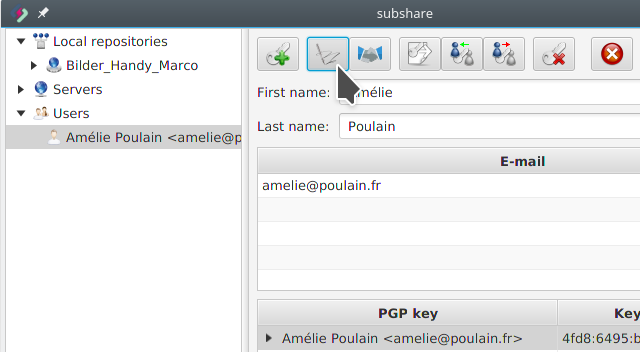
Adam certifies Amélie’s key (step 2)
The following dialog opens:
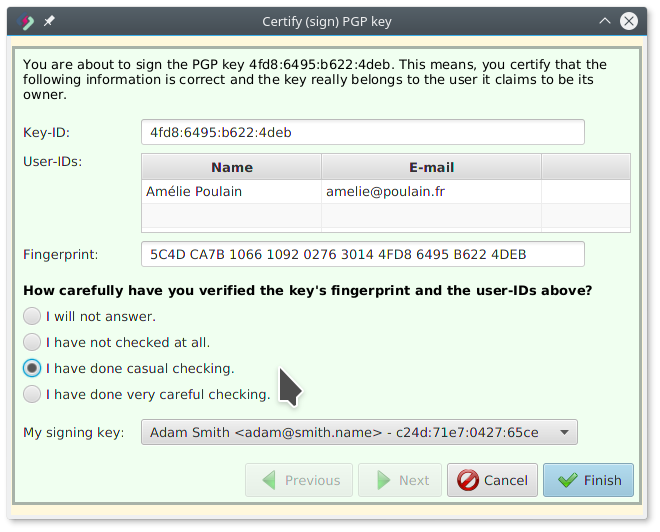
Adam calls Amélie by phone and asks her to read her key’s fingerprint to him.
Because Amélie does not know her own key’s fingerprint, she looks it up by opening the same dialog on her computer (and later cancels it).
She reads “5C4D…4DEB” (yes, all of it!) and Adam knows, everything is fine.
But because a telephone call isn’t as reliable and could be faked (though this is really hard, it is not impossible), Adam ticks I have done casual checking (had he met her personally, he could have done a very careful check).
Finishing this wizard means Adam officially certifies that the key is Amélie’s key. This information is used by him (his computer from now on trusts Amélie’s key) and it may be used by others (Web of trust).
Though it might look a bit inconvenient, this procedure is necessary to ensure that the key downloaded by Adam really belongs to Amélie:
If an attacker intercepted the communication between Adam’s computer and the server and succeeded to replace Amélie’s key, Adam would have found out now, because Amélie had read a different fingerprint to him.
If you want to understand this better, please read Public key fingerprint.
Adam invites Amélie (step 1)
Adam selects the repository he wishes to share and clicks the Invite button:
Please note, that it is also possible to share a sub-folder instead of the entire repository. For this purpose, simply navigate through the repository/folder tree and select the directory you wish to share:
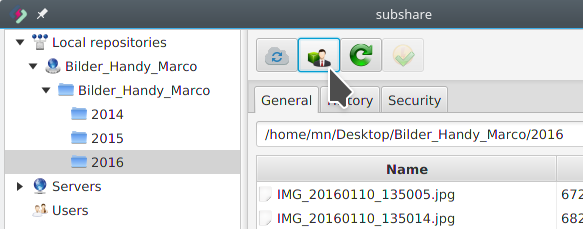
However, in this example, Adam shares his entire repository with Amélie.
Adam invites Amélie (step 2)
Adam selects Amélie and clicks Next:
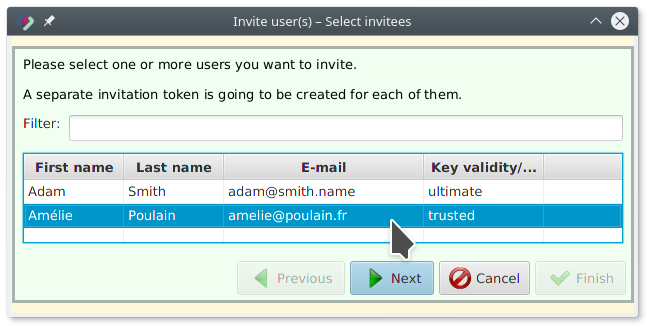
Adam invites Amélie (step 3)
Adam wants the invitation file to be saved on the Desktop:
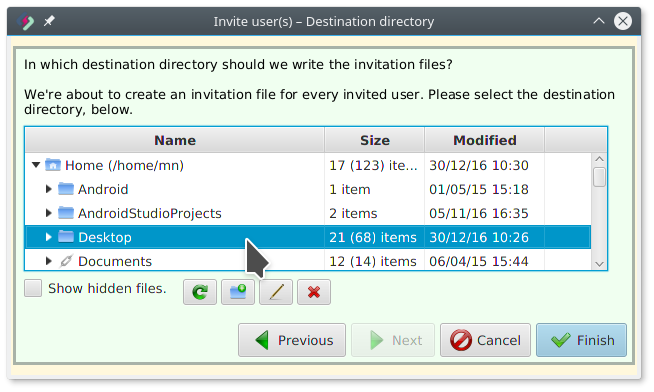
Adam invites Amélie (step 4)
The invitation file was created:
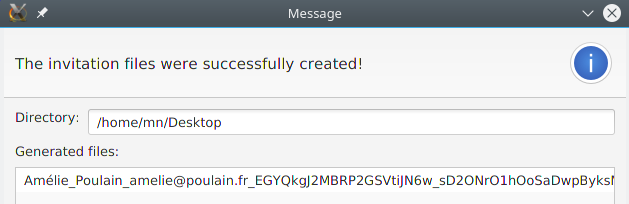
Adam now sends this file to Amélie by e-mail (or chat or whatever communication channel he prefers).
Amélie accepts the invitation (step 1)
Amélie clicks the Accept invitation button:
Amélie accepts the invitation (step 2)
Amélie selects the invitation file:
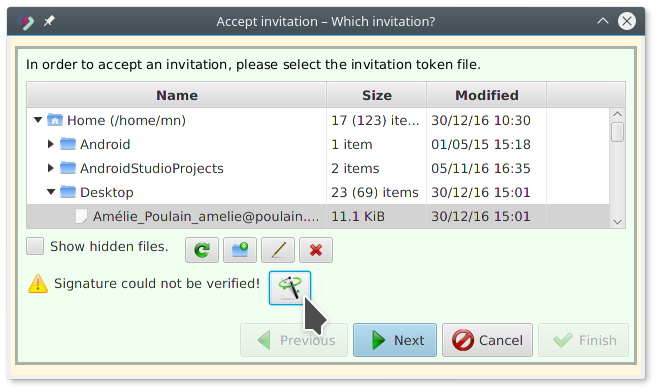
Because Amélie did not yet import Adam’s key, there is a warning. If she clicks the Solve button behind it and imports the key, an error marker instead tells her that the key is not trusted.
It is not required, but strongly recommended that Amélie also verifies (and certifies) Adam’s key. Depending on how Amélie received the invitation file, it is possible (though unlikely), that not Adam, but an attacker signed the invitation with a fake key.
Amélie accepts the invitation (step 3)
Amélie created the folder ~/Desktop/000_subshare/Adams_Pictures/ for Adam’s repository and selected it:
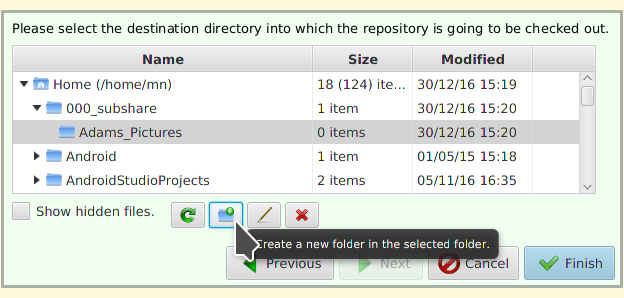
Clicking Finish now starts the check-out process.
Important: This turns the selected folder directly into the root of the checked-out working copy! There won’t be any further intermediate folder for the new repository.
That’s it!
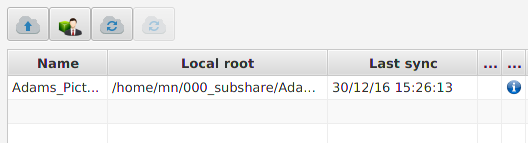
The new repository is now listed with the status “in progress”:
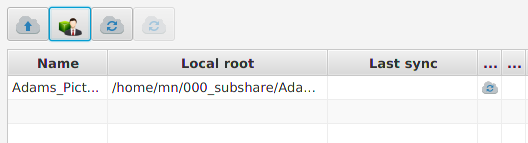
Depending on the size of the data and the internet connection speed, this can take a while (minutes, hours or even days). You don’t need to wait. It’s safe to interrupt subshare. It resumes where it was interrupted, when you start it again.
Once it’s done, the cloud-icon disappears and the blue info-icon is shown instead: