Frequently asked questions (FAQ)
What’s OpenPGP and why does subshare use it?
The OpenPGP and Security pages answer this question.
What encryption algorithms are used?
Whenever OpenPGP is involved, the properties of the OpenPGP keys used dictate the public-key algorithm. When subshare creates a new OpenPGP key, it generates an RSA key with a size of 4096 bit.
For the OpenPGP-based symmetric encryption, Twofish (with 256 bit keys) is used.
Most of the encryption and signing is done without OpenPGP (see Security), though. For these thousands of non-OpenPGP-based keys and cipher-operations, subshare uses:
What happens in case of a collision?
If you modify the same file on two separate computers and then synchronise, there is - obviously - a collision. You also run into a collision, if you modify a file on one device and delete it on another (without synchronising inbetween). There are more situations leading to collisions, of course, but there's no need to list them all here.
All collisions are solved in the same way: Both versions are checked-in so that both are available in the history (and can be restored), a collision-marker is created for the affected file/directory and shown in the UI (in the directory tree as well as in the history).
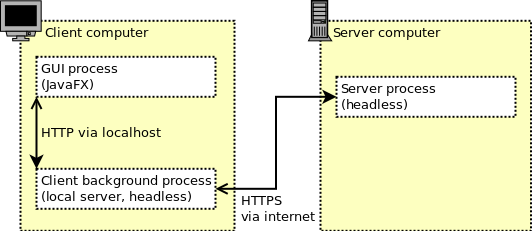
What’s this “local server”?
Subshare’s client program consists of two parts: The graphical user interface (GUI) and the actual logic. The two parts run in two distinct processes (JVMs), allowing for the GUI to be closed, while the synchronisation continues to run in the background.
When you start the GUI process, it automatically launches the so-called cproc (client process) with the local server in the background — if it is not yet running.
The local server opens a randomly chosen TCP port on localhost and is thus not accessible from other computers. To protect it further, i.e. to prevent other users on the same computer from accessing it, the local server generates a random password on every startup. This password (together with its port) is stored in ~/.subshare/localServer.properties and thus not accessible to other users (if the file system permissions are set correctly).
The user can thus start subshare whenever he logs in into his workstation. After entering his OpenPGP secret key’s passphrase, he can quit the GUI process — the actual synchronisation logic continues to run and keeps everything in-sync.
How can I set log levels?
You can find all logging configuration files in the ~/.subshare directory.
There are :
- logback.client.xml for the client process
- logback.localserver.xml for the client’s separate server process (see “local server” above)
- logback.server.xml for the server process
Please consult the logback manual for further information about how to configure the logging.
Can I use subshare on my Android-based smart phone or tablet?
Currently, this is not yet possible. Sorry! But we’re working on it — see issue 32.
If you want to see this happen faster, you can financially support us (contact us then) or you can contribute as a developer.
Can I use subshare on my iOS-based smart phone or tablet?
No.
We do not sacrifice our precious time and money to support a company devoted to enjailing their users and developers! There are too many reasons not to use Apple to list them here.
In short: subshare is our contribution to making this world a better place. We certainly won’t donate our time to an evil company which pursues the opposite goal.
However, if you really want to use subshare on an iThing, you can pay us. If you’re serious about and financially capable to pay our efforts, please contact us.
Alternatively, you can develop & contribute it yourself.
What’s the relation and what are the differences between CloudStore and subshare?
CloudStore also synchronizes files between computers. subshare actually builds on top of CloudStore.
CloudStore solely protects the communication between client and server via encryption. The files are stored in plain-text on both client and server. This is great when your server is safe and completely under your control.
subshare, however, does not trust the server. It assumes that the server is NSA-controlled ;-) Therefore, all data reaching (and being stored on) the server is encrypted. Only the user owning the data and the users having been granted read permissions are able to decrypt the files.
Another question?
If your question is not answered here, please check both our wiki and our tracker.
If you still don't find what you're looking for, go ahead and ask your question publicly in the tracker. Please label your question as "question" there.